Secure applications identities and protect sensitive data
Trusted by leading organizations
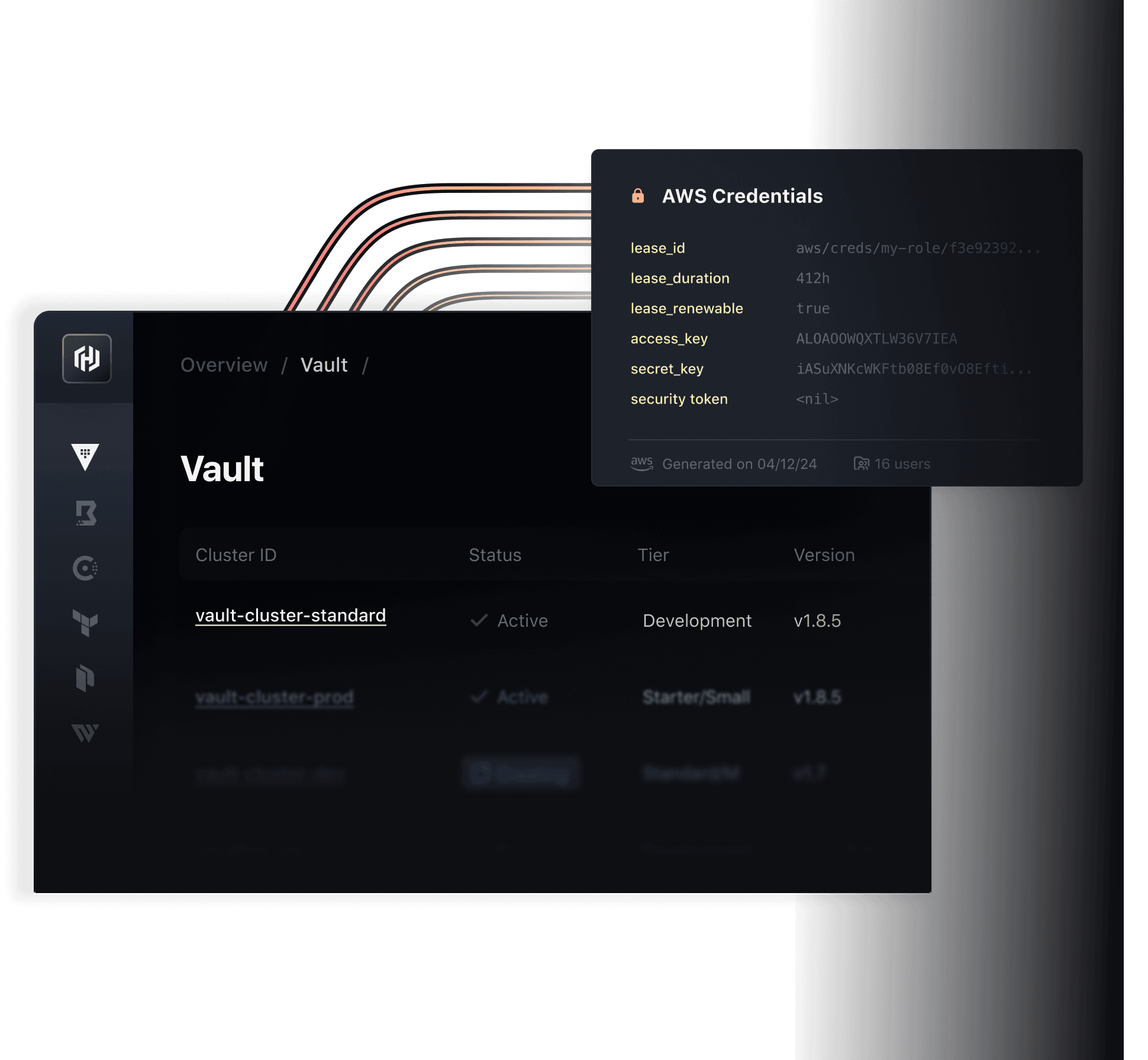
Secure credentials for secrets, certificates, keys, and more
Vault provides organizations with identity-based security to automatically authenticate and authorize access to secrets and other sensitive data.
- SecretsCentrally store, access, and distribute secrets programmatically.
- CertificatesGenerate, rotate, and revoke certificates on demand.
- KeysDistribute, rotate, enable, and disable keys.
- Data protectionProtect data in transit and at rest with encryption as a service.
Do cloud right with end-to-end secrets management

Avoid becoming the next data breach headline. Block unauthorized users by authenticating access based on trusted identities. Fight secret sprawl by using short-lived, just-in-time credentials that expire automatically.
Stop manually rotating secrets. Vault lets you use code to enforce access policies and speed up audits for your team. Use one API to automate secret creation, consumption, expiration, and rotation.
Lower costs by scaling access to secrets across large IT environments. Consolidate redundant secret storage applications by replacing them with Vault.
 When we were looking for a solution, one of the things we really cared about was extensibility, and Vault really shines on this. It's really pluggable, with the ability to develop custom auth engines and secrets engines, which means the runway is unlimited.Anthony Ralston
When we were looking for a solution, one of the things we really cared about was extensibility, and Vault really shines on this. It's really pluggable, with the ability to develop custom auth engines and secrets engines, which means the runway is unlimited.Anthony Ralston
Senior Software Engineer, Cloud Security, Canva The zero trust security framework will be really valuable for us when it’s fully implemented. It’ll allow us to verify and authorize every request made to our infrastructure, which can help to prevent unauthorized access and data breaches while delivering a high-performance, high-availability platform that underpins our customers’ businesses.Josh Scott
The zero trust security framework will be really valuable for us when it’s fully implemented. It’ll allow us to verify and authorize every request made to our infrastructure, which can help to prevent unauthorized access and data breaches while delivering a high-performance, high-availability platform that underpins our customers’ businesses.Josh Scott
Principal Engineer, Simpli.fi Along with policy-driven infrastructure through Terraform, Vault automatically rotates credentials instead of forcing users to store information locally and risk inadvertent exposure. Add in Boundary for standardizing language and protocols for accessing infrastructure and services across our environment, and it creates an end-to-end security posture in line with our zero trust charter.Benjamin Lara
Along with policy-driven infrastructure through Terraform, Vault automatically rotates credentials instead of forcing users to store information locally and risk inadvertent exposure. Add in Boundary for standardizing language and protocols for accessing infrastructure and services across our environment, and it creates an end-to-end security posture in line with our zero trust charter.Benjamin Lara
Automation Engineer, ManTech Before Vault, I’d spend at least three or four full days per month manually managing and rotating keys, but now it takes less than five minutes. Vault has simultaneously lowered how much effort it takes to meet regulatory compliance goals and reduced our risk of both a breach and unplanned downtime. It’s been amazing.Jannik Nolte
Before Vault, I’d spend at least three or four full days per month manually managing and rotating keys, but now it takes less than five minutes. Vault has simultaneously lowered how much effort it takes to meet regulatory compliance goals and reduced our risk of both a breach and unplanned downtime. It’s been amazing.Jannik Nolte
Information Technology Security Specialist, NORD/LB




Protect, inspect, and connect across all environments
Continuously protect credentials and other secrets, inspect the digital estate for unsecured secrets, and connect authorized machines.
- Protect secretsProtect sensitive data with a system of record and manage the full lifecycle of secrets, certificates, passwords, and keys.
- Inspect sensitive elementsInspect code repositories and collaboration tools to identify unsecured or unmanaged credentials.
- Connect machines, people, and networksConnect machines, people, and networks using trusted identities to authenticate and authorize every request.
Take control of your security estate
Trust no one. Instead, use identity-based controls to protect, inspect, connect, and manage the lifecycle of your secrets, users, machines, services, and data.
Get started with Vault
Start securing and simplifying workflows for secret lifecycle management in minutes.